|
.Technova
|
Computer Forensics-New Vistas In Evidence TechnologySharique M. Rizvi (shariq@iiita.ac.in) Dr. Madhvendra Misra (madhvendra@iiita.ac.in) Faculty, IIIT A
Abstract
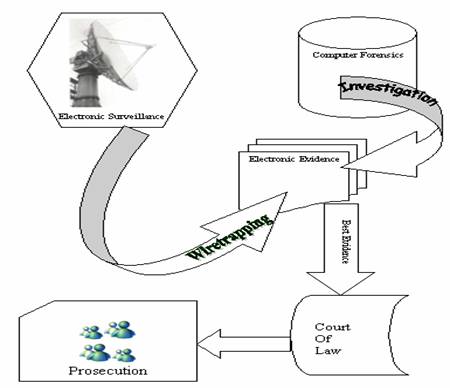
The paper explores the issues related to the relevance of a complex area of practice in field of cyber crimes, which has given new dimensions to the evidence and evidence related laws. Electronic evidence and their collection presentation, and testing have opened up a challenge to judiciary for its appropriate interpretation and assortment with valid sections of competent laws. The prevalence of cyber crime in digitalized world and has been scrutinize under the ambit of hi-tech involvement in computer forensics. The paper checks the procedures of identification of the source of electronic evidence, search and seizure, precaution to maintain the sanctity of the original evidences, maintaining and cross checking the integrity of the evidence collected. Collection and classification procedures and also throws light on process of presenting the evidence insuring it to be considered as best in the court of law. Key words:Computer Crime; Electronic Surveillance & Evidence; Computer Forensics; Search and Seizer Introduction Law is said to be the set pattern of desirable conduct for individuals and groups living in system. It pertinence is held and up held only by the virtue of time and the association of subjects to formalized geographical bounders. With changes of time culture and requirements the legal interpretation and their scope has found new meanings. With the advent of the third revolution and mass digitalization of the world the legal ambit and prospective has increased its cover on the virtual environment. The dynamics of the environment and the changes, which have occurred, has not affected the soul of law and legislation, which embodied in it self the cause to “to support and reinforce belief in law of the land and the civic society.” In the change prospective of time and scope wherein the consistency and association with a formal geographical boundary should be considered as a shortcoming in the capability of law to provide relief to affected parties. The challenge, which the legal system faces at hand of innovative technologies like Computers, Internet and others is immense and effects the capability of the legal system largely. Although the judiciary empowered by constitution and other legislations updated and upgraded from time to time has been discharging its functions effectively, there are still avenues and challenges to which Science and Technology has to cater and provide solutions. The judicial process specifically in consideration with the cyber world involves issues like crime accomplished and abetted through electronic or digital devices, resulting into a complex array of investigative and supportive activities. Which formally create a chain of process involving classification of the essential unlawful act (computer crime), preventive and post occurrence surveillance (electronic surveillance), extraction of useful information from used devices to unfold the act of crime (computer forensics) and finally enabling presentation in the competent court of law. Where: A Computer Crime is a crime committed with the aid of, or directly involving, a data processing system or network , with crime and viruses and hacking reportedly reaching epidemic proportions. The areas of greatest impact are laptop theft, data or network sabotage, virus and Trojan infection, computer fraud, denial of service attacks and excessive network resource consumption through external scams.
Electronic Surveillance and Prosecution Electronic Surveillance is an invaluable tool for fighting digital crime, investigating agencies cites many instances where criminal activities were either subverted, or if crimes were perpetrated, those responsible were apprehended as a result of electronic surveillance by law enforcement agencies. Computer forensics is defined throughout the paper as the use of an expert to preserve, analyze, and produce data from volatile and non-volatile media storage. This is used to encompass computer and related media that may be used in conjunction with a computer as electronic evidence in a court of law it involves obtaining and analyzing digital information for use as evidence in civil, criminal or administration cases it is the scientific examination and analysis of data held on, or retrieved from, computer storage media in such a way that the information can be used as evidence in a court of law. Practices engaged in by law enforcement officers in order to gain sufficient evidence to ensure the arrest and conviction of an offender. The latitude allowed police and other law enforcement agents in carrying out searches and seizures varies considerably from country to country Search and Seizure Search and seizure of digital evidence is the first process that is often disputed. If it is not completed properly, the defense or prosecution's evidence may not be admitted. An illegal search and seizure or improper methodology employed during search and seizure can negatively affect the admissibility of the evidence A unique issue with computer forensics search and seizure centers on the source of the items in the warrant or in verbal/written affirmation, when a warrant is not needed (e.g., open view resulting in a search and seizure). For instance, when a computer has the power turned off, the data in volatile media storage, for technical purposes, is virtually impossible to reconstruct. In pre-digital crimes, electricity was not a major factor in the ability to execute a proper search and seizure. i.e. Volatile media storage. Aaron Caffrey, the defendant, was arrested under the suspicion of launching a denial of service attack against the Port of Houston 's systems on September 20, 2001 . The defense argued that the Trojan was installed on the defendant's computer by the others who wanted to frame him for the attack The Trojan launched the attack from the defendant's computer but the defendant was not aware of the attack. The forensics examination showed that there was no sign of a Trojan, only attack tools on the computer, but could not rule out that a Trojan may have been in volatile storage media (random access memory). The jury unanimously decided that the defendant was not guilty. Though courts may grant a search and seizure warrant, law enforcement may ask individuals for verbal or written consent searching and seizing items. However, the voluntary nature of consent may vary. In Williford v. Texas , the appellant complained that the search and seizure of his computer was illegal. The appellant contended that his consent to the search and seizure was tainted and, as there was no warrant, there was no probable cause. The judge dismissed the claim. In U.S. v. Habershaw, the issue was whether the officers involved had the right to search and seize the computer, and if the defendant was capable of giving consent. The defendant argued that the warrant went “overboard.” The defendant gave verbal permission for the officers to operate his computer after the defendant stated the possible location of contraband child pornography images on the computer. Searching and seizing computers raises unique issues for law enforcement personnel that will influence the government's search and seizure decisions. Searching or seizing computers, not referring only to the CPU (Central Processing Unit) but it consists of input (e.g., a keyboard or mouse) and output (e.g., a monitor or printer) devices. These devices, known as "peripherals,"' are an integral part of any "computer system." Failure to more specifically define the term "computer" may cause misunderstandings. Having probable cause to seize a "computer" does not necessarily mean there is probable cause to seize the attached printer. Hardware "The physical components or equipment that makes up a computer system....". Examples include keyboards, monitors, and printers. Software "The programs or instructions that tells a computer what to do." This includes system programs, which control the internal operation of the computer system such as Disk Operating For search and seizure purposes, unless the text specifically indicates otherwise, the term "computer" refers to the box that houses the CPU, along with any internal storage devices such as internal hard drives and internal communications devices such as an internal modem or fax card. It is important to remember that computer systems can be configured in an unlimited number of ways with assorted input and output devices. In some cases, a specific device may have particular evidentiary value. “A bookie who prints betting slips, the printer may constitute valuable evidence; in others, it may be the information stored in the computer that may be important. In either event, the warrant must describe, with particularity, what agents should search for and seize” . The computer system may be a tool of the offense. This occurs when a defendant to commit the offense actively uses the computer system. For example, a counterfeiter might use his computer, scanner, and color printer to scan currency and then print money. Second, the computer system may be incidental to the offense, but a repository of evidence. For example, a drug dealer may store records pertaining to customers, prices, and quantities delivered on a personal computer, or a blackmailer may type and store threatening letters in his computer. In each case, the role of the computer differs. It may constitute "the smoking gun" (i.e., be an instrumentality of the offense), or it may be nothing more than an electronic filing cabinet (i.e., a storage device). In some cases, the computer may serve both functions at once. Hackers, often use their computers both to attack other computer systems and to store stolen files. In this case, the hacker's computer is both a tool and storage device. By understanding the role that the computer has played in the offense, it is possible to focus on certain key questions: • Is there probable cause to seize hardware? • Is there probable cause to seize software? • Is there probable cause to seize data? • Where will this search be conducted? The principles of Fourth Amendment, Constitution of United States of Americas apply to computer searches, and traditional law enforcement techniques may provide significant evidence of criminal activity, even in computer crime cases. To determine whether an individual has a reasonable expectation of privacy in information stored in a computer, it helps to treat the computer like a closed container such as a briefcase or file cabinet. The Fourth Amendment generally prohibits law enforcement from accessing and viewing information stored in a computer without a warrant if it would be prohibited from opening a closed container and examining its contents in the same situation. The questions looming large in the minds of investigation agency and makers of the law was aptly answered by the fourth amendment in the US Constitution, which in principle uphold the integrity of individual privacy with only certain exceptions giving limited privileges to investigation and enforcement agencies. The Indian Telegraph Act upholds the privacy in an individual significantly limiting surveillance and seizer of electronic information only under exception of affecting public safety and tranquility. Whereas incases of terrorist and anti national activities individual privacy seizes to exist.
Provisions in Indian Telegraph Act The Indian Telegraph Act authorizes the surveillance of communications, including monitoring telephone conversations and intercepting personal mail, in case of public emergency or "in the interest of the public safety or tranquility." Every state government has used these powers. The Union Government also uses the powers of the Indian Telegraph Act to tap phones and open mail. The Indian Telegraph Act of 1885 authorizes the surveillance of communications, including monitoring telephone conversations and intercepting personal mail, in cases of public emergency, or "in the interest of the public safety or tranquility." The central Government and every state government used these powers during the year. Although the Telegraph Act gives police the power to tap phones to aid an investigation, they were not allowed to use such evidence in court; however, under POTA and the (UAPA) Unlawful Activities Prevention Act such evidence was admissible in terrorist cases, and some human rights activists noted that the new UAPA Ordinance confers additional powers on police to use intercepted communications as evidence in terrorism cases. While there were elaborate legal safeguards to prevent police from encroaching on personal privacy, there were no such protections in terrorist cases.
Electronic Surveillance and the Fourth Amendment The Olmstead Case. —With the invention of the microphone, the telephone, and the dictograph recorder, it became possible to ‘‘eavesdrop'' with much greater secrecy and expediency. Inevitably, the use of electronic devices in law enforcement was challenged, and in 1928 the Court reviewed convictions obtained on the basis of evidence gained through taps on telephone wires in violation of state law. On a five-to-four vote, the Court held that wiretapping was not within the confines of the Fourth Amendment. Chief Justice Taft, writing the opinion of the Court, relied on two lines of argument for the conclusion. First, inasmuch as the Amendment was designed to protect one's property interest in his premises, there was no search so long as there was no physical trespass on premises owned or controlled by a defendant. Second, all the evidence obtained had been secured by hearing, and the interception of a conversation could not qualify as a seizure, for the Amendment referred only to the seizure of tangible items. Furthermore, the violation of state law did not render the evidence excludible, since the exclusionary rule operated only on evidence seized in violation of the Constitution.
The Berger and Katz Cases. —In Berger v. New York , the Court confirmed the obsolescence of the alternative holding in Olmstead that conversations could not be seized in the Fourth Amendment sense. Berger held unconstitutional on its face a state eavesdropping statute under which judges were authorized to issue warrants permitting police officers to trespass on private premises to install listening devices. The warrants were to be issued upon a showing of ‘‘reasonable ground to believe that evidence of crime may be thus obtained, and particularly describing the person or persons whose communications, conversations or discussions are to be overheard or recorded.'' For the five-Justice majority, Justice Clark discerned several constitutional defects in the law. ‘‘First, . . . eavesdropping is authorized without requiring belief that any particular offense has been or is being committed; nor that the ‘property' sought, the conversations, be particularly described.
Warrantless ‘‘National Security'' Electronic Surveillance. — In Katz v. United States , Justice White sought to preserve for a future case the possibility that in ‘‘national security cases'' electronic surveillance upon the authorization of the President or the Attorney General could be permissible without prior judicial approval. The Executive Branch then asserted the power to wiretap and to ‘‘bug'' in two types of national security situations, against domestic subversion and against foreign intelligence operations, first basing its authority on a theory of ‘‘inherent'' presidential power and then in the Supreme Court withdrawing to the argument that such surveillance was a ‘‘reasonable'' search and seizure and therefore valid under the Fourth Amendment. Unanimously, the Court held that at least in cases of domestic subversive investigations, compliance with the warrant provisions of the Fourth Amendment was required.
The Communications Assistance For Law Enforcement Act (P.L. 103-414) An affirmative obligation for telecommunication service providers to assist the law enforcement community in authorized electronic intercepts, The Supreme Court in United States v. New York Telephone , In (1977) found that 18 U.S.C. 2518(4) required the federal courts to compel telecommunication providers to provide “any assistance necessary to accomplish an electronic interception.” The question of whether a carrier has any obligation to design its equipment to facilitate an authorized electronic surveillance under 8 U.S.C 2518(4) was never litigated. The Communications Assistance For Law Enforcement Act makes it clear that the service providers must now consider equipment and system design as well as the capability to provide the call content and call Identification information needed by law enforcement agencies, and the capacity that the law enforcement agencies need to simultaneously intercept a specified number of wiretaps. The Act also establishes a process for reimbursing the service providers for their expenses in meeting law enforcement's needs. The amendment requires the service provider “furnish the information, facilities, and technical assistance necessary to accomplish the interception . . . . .” The amendment further provides that a cooperating service provider to be compensated for reasonable expenses incurred in providing such facilities or assistance.
Requirement 1 • Law enforcement agencies require access to the electronic communications transmitted, or caused to be transmitted, to and from the number, terminal equipment, or other identifier associated with the intercept subject throughout the service areas operated by the service provider served with a lawful authorization. Law enforcement agencies also require access to generated call-identifying information necessary to determine the calling and called parties. Law enforcement agencies will coordinate delivery of these communications with the service provider in accordance with requirement for each service area. • Law enforcement agencies require real-time, full-time monitoring capability for interceptions. • Law enforcement agencies require telecommunications carriers to make provisions for implementing a number of simultaneous interceptions. • Law enforcement agencies require telecommunications carriers to expeditiously provide access to the communications of the intercept subject. Requirement 2 Law enforcement agencies require:
Requirement 3
Requirement 4
In the case of a Cyber Crime pursued by the Police "Evidence" plays a vital part in securing the interests of the Information Asset owner. The legal requirements and the devices required for the purpose of collecting judicially acceptable Cyber Evidence. The necessary amendments were made to the Indian Evidence Act 1872 by the Information Technology Act 2000 (ITA-2000). In the case of electronic documents produced as "Primary Evidence", the document itself must be produced to the Court. However, such electronic document obviously has to be carried on a media and can be read only with the assistance of an appropriate Computer with appropriate operating software and application software. In many cases even in non-electronic documents, a document may be in a language other than the language of the Court in which case it needs to be translated and submitted for the understanding of the Court by an "Expert". Normally the person making submission of the document also submits the translation from one of the "Experts". If the counter party does not accept the "Expert's opinion", the court may have to listen to another "Expert" and his interpretation and come to its own conclusion of what is the correct interpretation of a document. In the case of the Electronic documents, under the same analogy, "Presentation" of document is the responsibility of the prosecution or the person making use of the document in support of his contention before the Court. Based on his " Reading " of the documents, he submits his case. This may however be disputed by the counter party. In such a case, it becomes necessary for the Court to "Get the document Read by an expert” to its satisfaction. It is necessary to have some clarity on the legal aspects of such documents presented to the Court because most of the court battles are expected to revolve around "Proper Reading " of the documents and "Possible manipulation of the documents". In making presentation of an "Electronic Document", the presenter may submit a readable form of the document in the form of a "Print Out". Question arises in such a case whether the print out is”Primary Evidence" or”Secondary Evidence". Indian Evidence Act, 1872 The key provisions that are made in Indian Evidence Act relate to widening of the scope of term document` to include electronic record. Most importantly, section 65B recognizes admissibility of computer outputs in the media, paper, and optical or magnetic form. There are detailed provisions relating to admissibility of computer output as evidence. New section 73A prescribes procedures for verification of digital signatures. New Section 85A and 85B create presumption as regards electronic contracts, electronic records and digital signatures, digital signature certificates and electronic messages.
Whether by design or otherwise, Section 65B clearly states that " Not withstanding anything contained in this (Indian Evidence Act) Act, any information contained in an electronic record which is printed on a paper, stored, recorded or copied in optical or magnetic media produced by a computer called the Computer Output shall be deemed to be also a document...."
However, for the "Computer Output" to be considered as admissible evidence, the conditions mentioned in the Section 65 B (2) needs to be satisfied. Section 65B(2) contains a series of certifications which is to be provided by the person who is having lawful control over the use of the Computer generating the said computer output and is not easy to be fulfilled without extreme care. It is in this context that the responsibility of the Law Enforcement Authorities in India becomes enormous while collecting the evidence. In a typical incident when a Cyber Crime is reported, the Police will have to quickly examine a large number of Computers and storage media and gather leads from which further investigations have to be made. Any delay may result in the evidence getting obliterated in the ordinary course of usage of the suspect hard disk or the media.
Any such investigation has to cover the following main aspects of Cyber Forensics, namely, 1. Collection of suspect evidence 2. Recovery of erased/hidden/encrypted data 3. Analysis of suspect evidence
The Best Evidence Rule (US) The best evidence rule states that to prove the content of writing, recording, or photograph, the “original” writing, recording, or photograph is ordinarily required. Agents and prosecutors occasionally express concern that a mere printout of a computer-stored electronic file may not be an “original” for the purpose of the best evidence rule. After all, the original file is merely a collection of 0's and 1's; in contrast, the printout is the result of manipulating the file through a complicated series of electronic and mechanical processes. Fortunately, the Federal Rules of Evidence have expressly addressed this concern. The Federal Rules state that, if data are stored in a computer or similar device, any printout or other output readable by sight, shown to reflect the data accurately, is an “original”. Thus, an accurate printout of computer data always satisfies the best evidence rule. (Holding that AOL Instant Message logs that police had cut-and-pasted into a word-processing file satisfied best evidence rule).
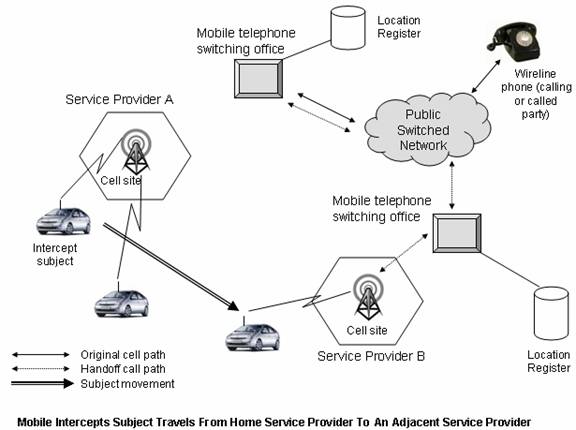
Indian Penal Code, 1860 A number of amendments have been made to sections 29, 167, 172, 192, 463, 464 and the like. The key amendment relates to the widening of term document to include electronic records. Section 464 now recognizes the concept of digital signature. The prevalence of mobile digital devices and there a potential involvement in perpetuating crime and criminal activities has proven to be a challenge to agencies involved in electronic surveillance. The problem of tracking with multiple service providers in different geographical areas has effected the capability of electronic surveillance systems where as services like roaming are useful to individuals but are cause of anarchical situations of investigations RoamingWhen roaming outside of the home service area, law enforcement requires access to all calls initiated or received by the subject if the visited service provider has received a lawful request to activate an intercept, and arrangements have been made for delivery of the information to the law enforcement-monitoring site. The visited service provider has no legal obligation to intercept a cellular target's calls once the subject moves out of its service area unless it is a call in process. The home cellular service provider is required to provide access to any call setup information or call content if access is maintained in the home area during call delivery to a roaming subject.
Registration InformationWhen a mobile intercept subject roams into a new service area, activates his or her mobile unit, and requests service, the home service providers Home Location Register (HLR) exchanges information with the new cellular service provider's Visiting location Register (VLR). When this occurs, law enforcement agencies require information on the identity of the new service area requesting the registration information. Law enforcement must then obtain a lawful authorization to access the call content and call setup information from the visited service provider. Conclusion The inevitable fact that technology is becoming more intertwined in the daily life of the individual will lead to an increase in court cases where computer evidence is a vital component. Because the judicial system is having difficulties in mandating and interpreting standardization for computer forensics, it becomes the responsibility of the scientific community to assist in this endeavor. In the evolution of the Indian challenge to Cyber Crimes, during the last three years, Police in different parts of the Country have been exposed to the reality of Cyber Crimes and more and more cases are being registered for investigation. However, if the Law enforcement does not focus on the technical aspects of evidence collection and management, they will soon find that they will be unable to prove any electronic document in a Court of Law. Now we have to embark on the next step of assisting the Law Enforcement in India with suitable Computer hardware and software that would enhance the quality of "Cyber Evidence" that can be produced to a court of law in case of any Cyber Crime. If the process of such collection, recovery and analysis is not undertaken properly, the evidence may be rejected in the Court of law as not satisfying the conditions of Section 65B of the Indian Evidence Act If the country that suffered damage wants to prosecute a culprit of foreign nationality, there has to be an extradition treaty with the country where the hacker is resident. Besides, the legal framework for proceeding with prosecution is still not certain. In spite of the extradition treaty, if a law allegedly broken in a country has no equivalent in the culprit's native country, there can be no prosecution. In developing countries including India , the problem is further compounded because of the lack of training of cops on subjects such as computer forensics to investigate into cyber crimes or of the adjudicating officers. This will adversely affect the fight against Cyber Crime. Unless the police is able to retrieve data from a computer, they would not be able to deal with the cyber crimes References: • Indian Information Technology Act 21 of 2000 • Indian Evidence Act 1872 • Indian Penal Code 1860 • Indian Telegraph Act 1885 • Forth Amendment Constitution of United States of America • The Communications Assistance For Law Enforcement Act (P.L. 103-414), US
GPO stock #052-003-01418-1 |