xSQLScanner Database Password Cracker & Security Audit Tool For MS-SQL & MySQL
xSQL Scanner is a advanced SQL audit tool created by SeCToR-X that allow user find weak passwords and vulnerabilities over MS-SQL and My-SQL protocols.
Assist the Security Analyst and Penetration Tester find weak passwords and vulnerabilities over MS-SQL and My-SQL protocols.
(http://culturecyber.blogspot.in/2012/02/xsql-scanner-advanced-sql-audit-tool.html)
Features :
- Test for weak password fast
- Test for wear/user passwords
- Wordlist option
- User list option
- Port scanner
- Range IP Address audit
Options and controls:
There are 3 buttons available:
Start, Stop and Save Results.
Also there is a menu with following items. Each control have their respective functions, that will allow user analyze and audit SQL servers. Actually the xSQL Scanner only supports MS-SQL and MySQL servers. The first control to handle is the Target Options.
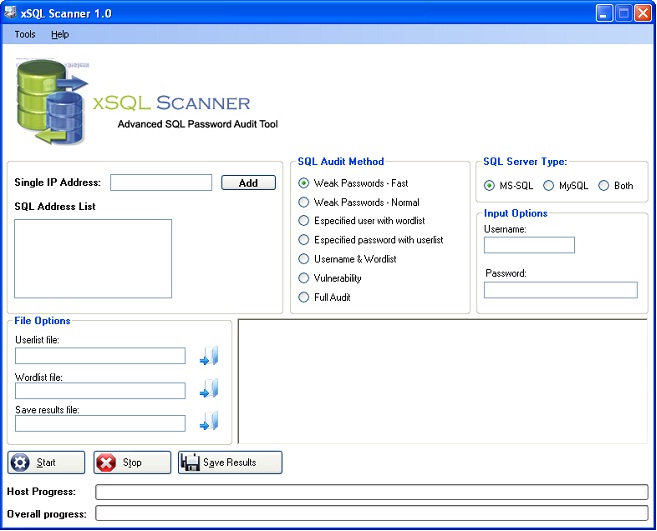
Target Options:
The target options will define the scope of SQL devices to be analyzed. It’s possible scan one target only. To do that, just supply the device IP Address on field ‘Single IP Address’ and then click on button ‘Add’.
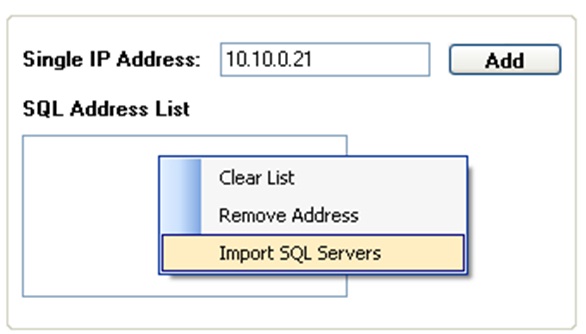
When is done, the application will add that IP Address to SQL Address List. Chose the necessary left options and click on ‘Start Button’. Also is possible adding multiple servers just repeating the process with different IP Address, however the xSQL Scanner allow load the IP Address servers from a file list. Right Click on SQL Address List, a context menu will appear on the screen with 3 options: Remove, Clear List and Import S–QL Servers. Choose the last one and then select the file with SQL server address.
Once defined the scope, the next step will be the Audit Type. There are 7 options available:
1. Weak Passwords – Fast: Will be tested weak passwords with username ‘sa’ or ‘root’ depending on the selected SQL Server type.
2. Weak Passwords – Normal: This option is similar to the one above, but common usernames will be tested against weak passwords.
3. Specified user with wordlist: A wordlist will be tested against the username supplied in ‘Username’ field under ‘Input Options’.
4. Specified password with wordlist: Supplied password in ‘Password’ field will be tested against usernames contained in file.
5. Username & Wordlist: Supplied wordlist and userlist will be tested against each other.
6. Vulnerability: This option detects common vulnerabilities of MS-SQL and MySQL based on banner version.
7. Full Audit: Execute vulnerability audit and tests for weak password.
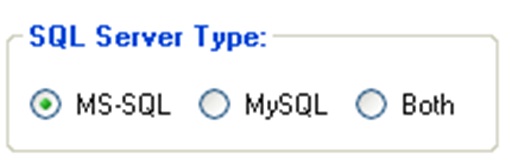
After choose the Audit Type, choose the SQL Server Type to Audit: MS-SQL, MySQL or Both. By default MS-SQL option will be used.
Depending of chosen Audit Type, may it be necessary fill the Input Options fields. There are two fields: Username & Password. The Username is required when the Audit Option is equal 3 and Password when is equal 4.
File Options may it be necessary too according with Audit Type chosen. There are 3 input fields in File Options section:
Userlist file: Choose a file with username list to be tested against passwords. This field will be used when Audit Option is equal 4.
Wordlist file: Choose a file with passwords to be tested against a single or multiple username. This field will be used when Audit Option is equal 3 or 5.
Save Results file: Choose a file to store application output.
Using xSQL Scanner:
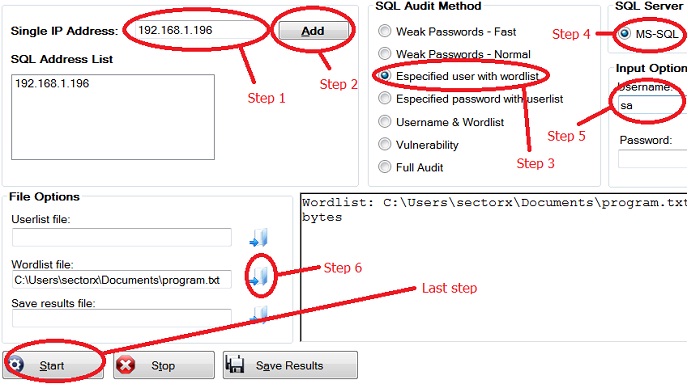
In this example will be used a wordlist called ‘program.txt’ and the server type will be MS-SQL. Also the audit method will be ‘Specified user with wordlist’. This option will make the application test passwords from a wordlist file against specified username.
1. You need type the IP address in ‘Single IP Address’ field;
2. Click in button ‘Add’;
3. Choose the Audit Method ‘Specified user with wordlist’;
4. Select MS-SQL in SQL Server groupbox;
5. Type the username ‘sa’ in Username field;
6. Load the wordlist clicking in ‘Wordlist file’ field;
7. Finally click in ‘Start’ button and wait results.
For downloading try this link:
( http://www.4shared.com/file/ykeEX3TV/xsqlscan-mono.html)By:
Ankur Sharmai
MS Cyber Law & Information Security
Indian Institute of Information Technology